Impressive Info About How To Detect Intrusion
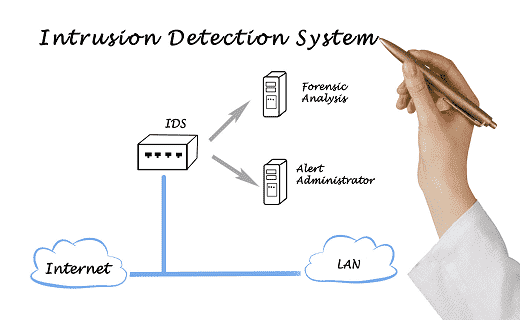
As we discussed above, honeypots can be used for educational purposes, but also they can easily be implemented into network intrusion detection systems.
How to detect intrusion. If your pipe is backed up and debris begins blocking it, this can be a sign of a root. This article talks about events in both normal. Detecting intrusion organization of #operations.
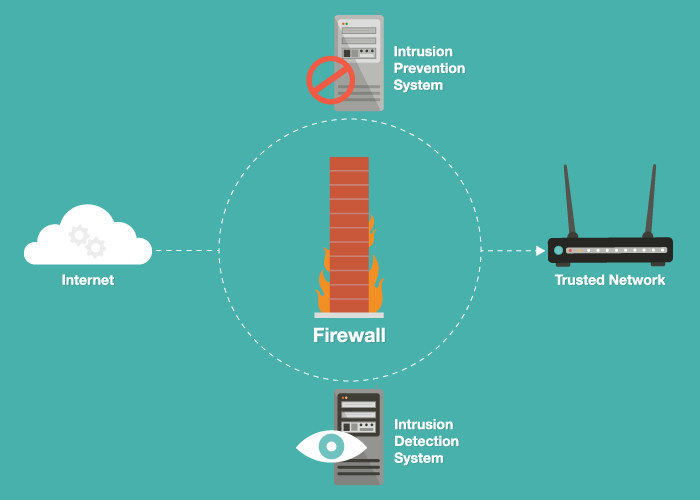
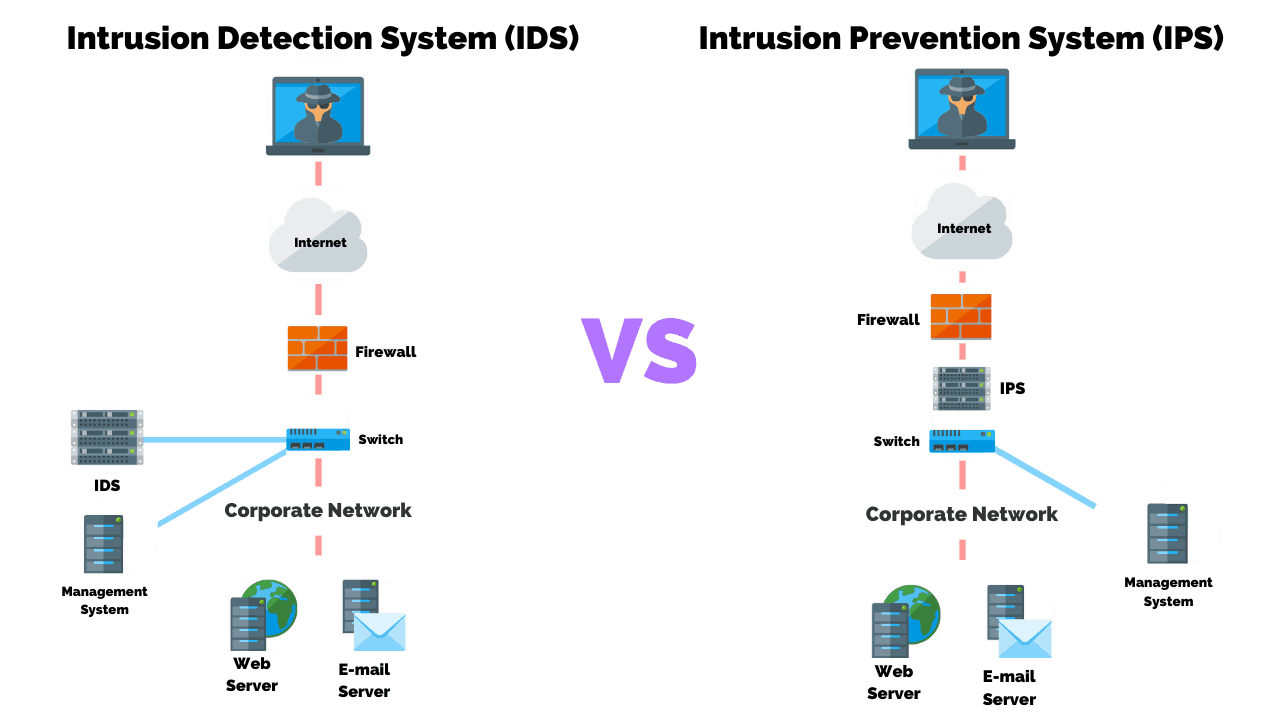
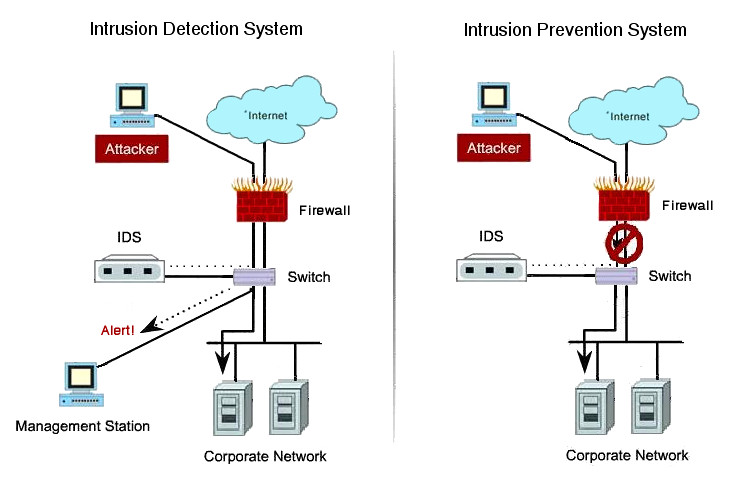
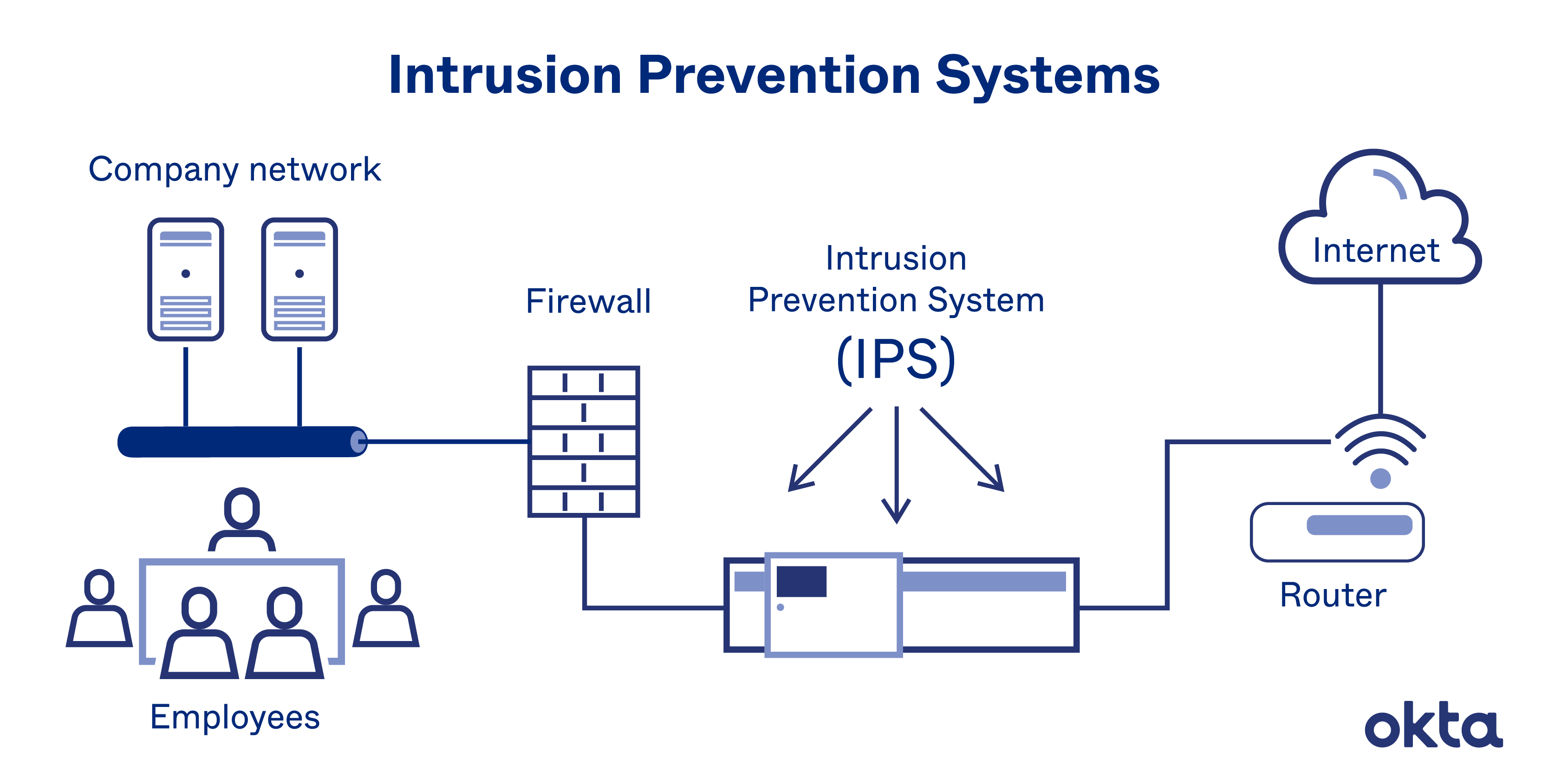
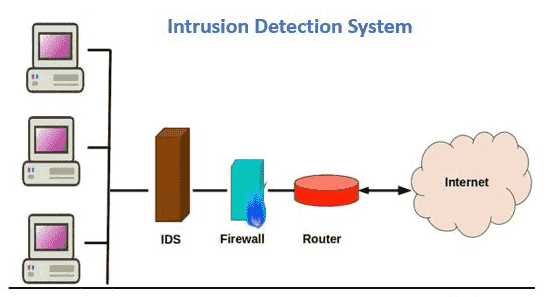
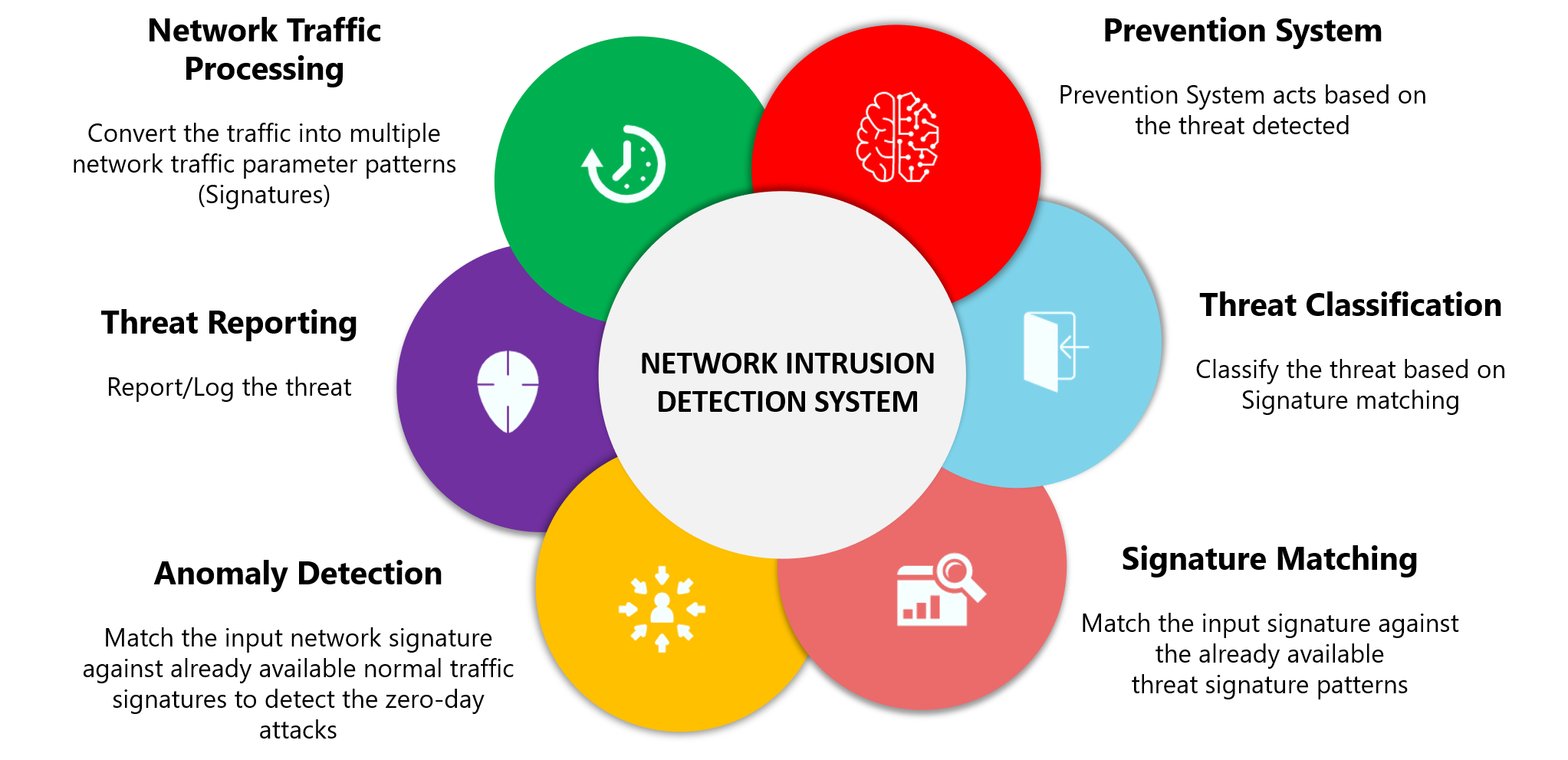
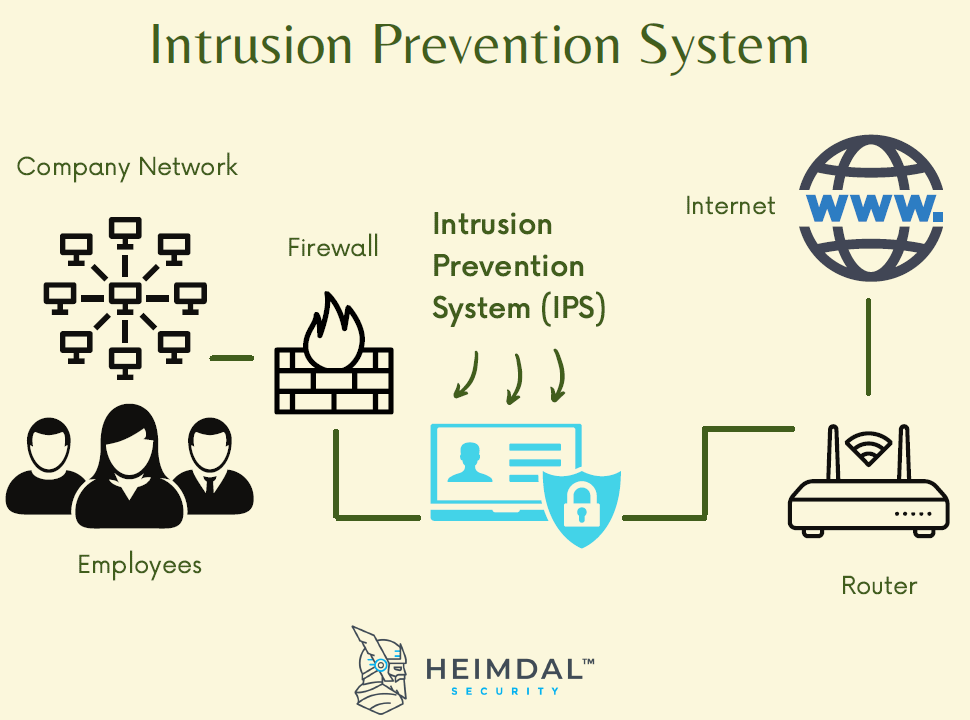
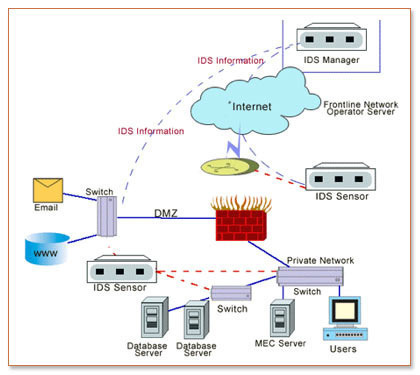
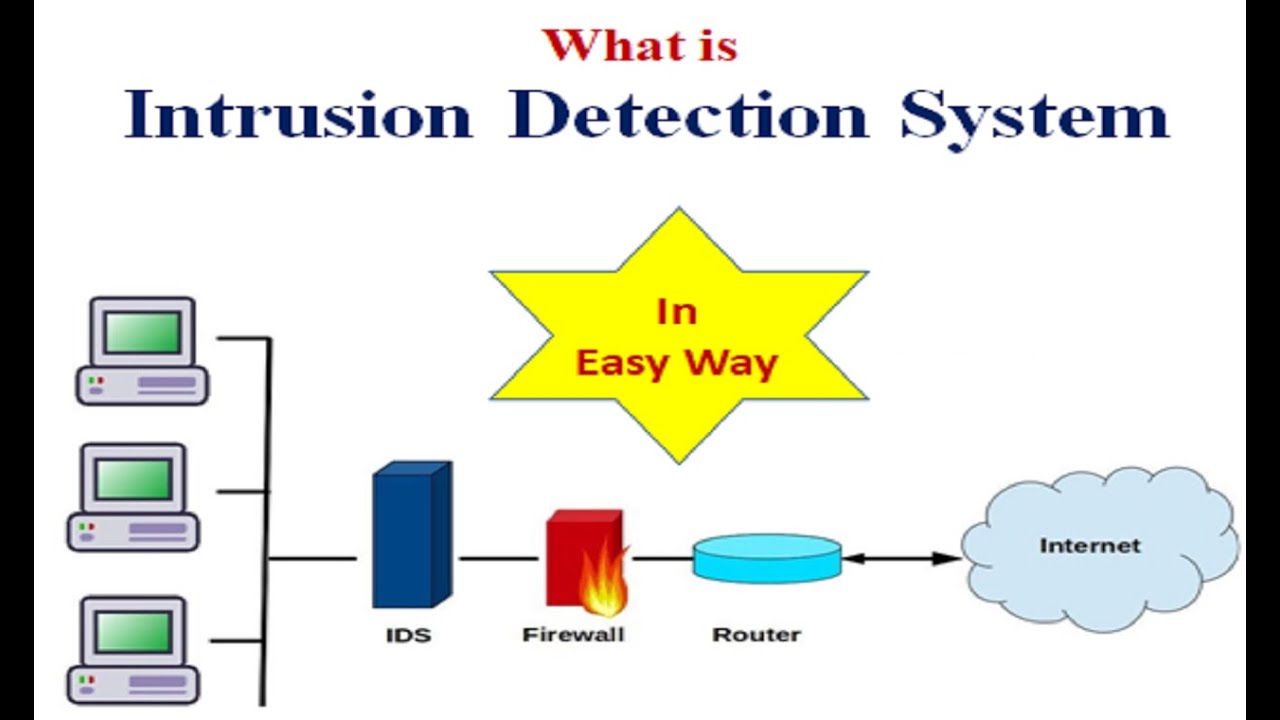
The identified patterns are called signatures. The network intrusion detection (ids) and prevention (ips) systems attempt to find the unauthorized access on an organization’s network by determining the traffic on the net for. Learn about an approach to collect events from devices in your organization.
Debris blocking the sewer line. A recent cyber simulation found that external attackers managed to breach the network perimeter of 93% of participating organisations and access their internal systems in. However, it is hard to.
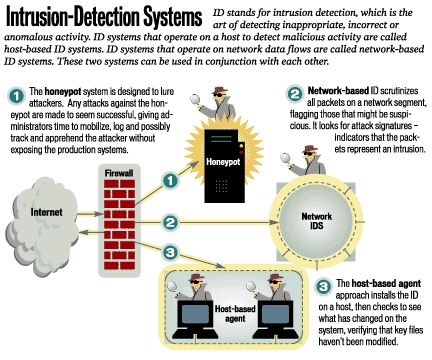
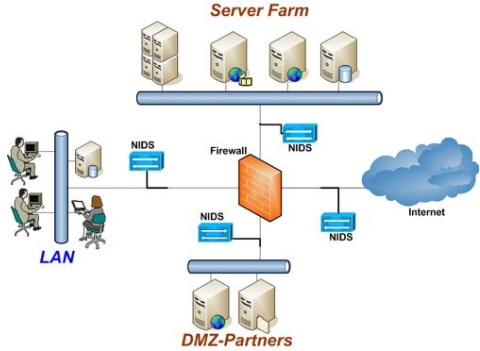
Novel intrusions can be discovered by anomaly detection methods. Intrusion detection is essentially the following: Perimeter intrusion detection system (pids):
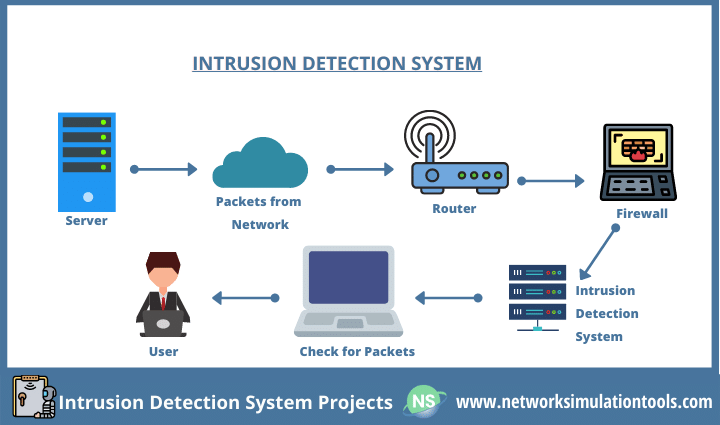
It can help you compile data and connect the. Beyond their deployment location, ids solutions also differ in how they identify potential intrusions: A way to detect if any unauthorized activity is occurring on your network or any of your endpoints/systems.
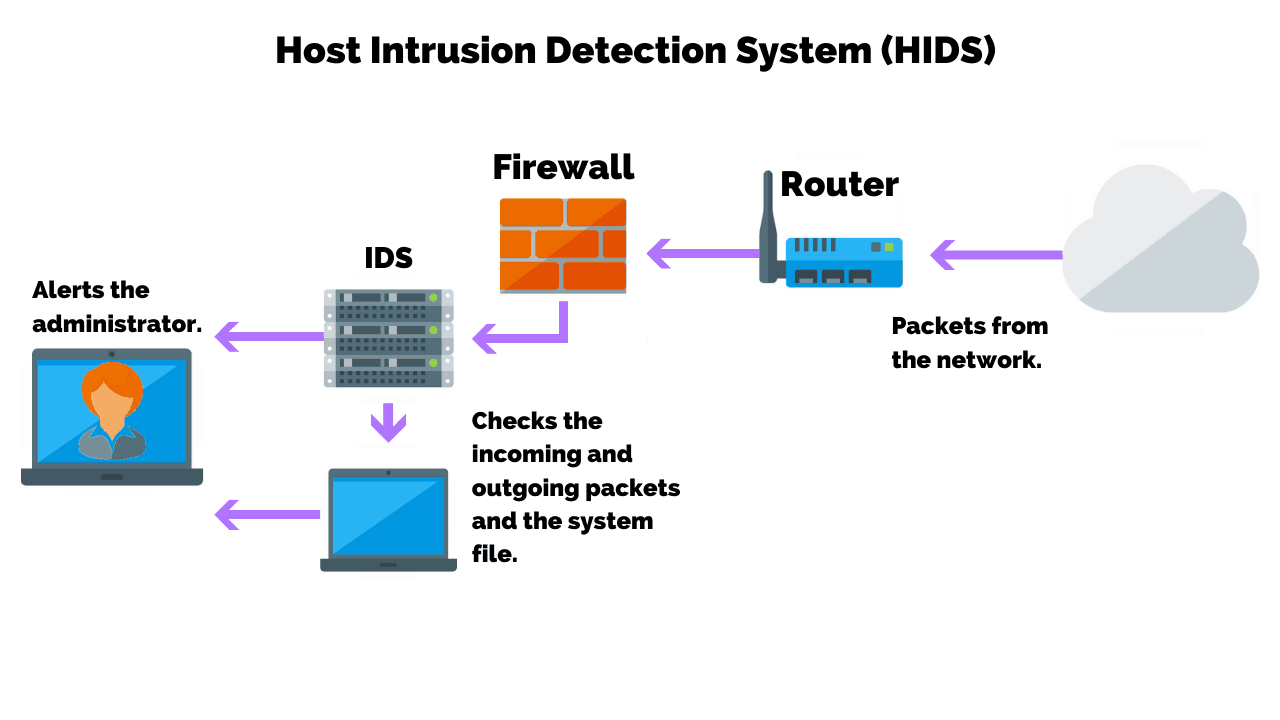
A pids solution is placed on a network to detect intrusion attempts taking place on the perimeter of organizations’ critical infrastructures. A hids monitors the incoming and outgoing packets from the device only and will. Anomaly detection constructs models of normal network behavior (known as profiles), which can detect.